漏洞版本
Discuz!X < 2.5.R20171001
Discuz!X < 3.4.R20170929
漏洞描述
漏洞存在source\include\spacecp\spacecp_profile.php中,$_FILES中包含未过滤的key值,控制space[‘key’]值可unlink任意文件。参考discuz小于R20140619前台任意文件删除漏洞
漏洞分析
$_FILES接收上传文件,通过一系列init(),save(),get_image_info的安全过滤,控制key值unlink(space[$key]),此处space为用户个人资料数组。1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17if($_FILES) {
$upload = new discuz_upload();
......
$upload->init($file, 'profile');
$attach = $upload->attach;
if(!$upload->error()) {
$upload->save();
if(!$upload->get_image_info($attach['target'])) {
@unlink($attach['target']);
continue;
}
$setarr[$key] = '';
$attach['attachment'] = dhtmlspecialchars(trim($attach['attachment']));
......
@unlink(getglobal('setting/attachdir').'./profile/'.$space[$key]);
$setarr[$key] = $attach['attachment'];
}
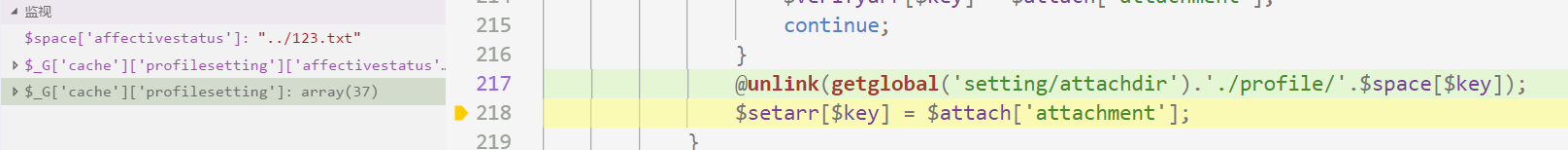
漏洞利用
- 修改个人资料情感状态处值为../123.txt,此处目录为\data\attachment\profile
- 查看元素修改情感状态type为file,并上传正常图片,保存即可删除指定文件。
漏洞修复
source\include\spacecp\spacecp_profile.php1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24$upload->init($file, 'profile');
$attach = $upload->attach;
if(!$upload->error()) {
$upload->save();
if(!$upload->get_image_info($attach['target'])) {
@unlink($attach['target']);
continue;
}
$setarr[$key] = '';
$attach['attachment'] = dhtmlspecialchars(trim($attach['attachment']));
if($vid && $verifyconfig['available'] && isset($verifyconfig['field'][$key])) {
if(isset($verifyinfo['field'][$key])) {
$verifyarr[$key] = $attach['attachment'];
}
continue;
}
if(isset($setarr[$key]) && $_G['cache']['profilesetting'][$key]['needverify']) {
$verifyarr[$key] = $attach['attachment'];
continue;
}
$setarr[$key] = $attach['attachment'];
}
23行unlink功能删除